Hosted agents code access
Buildkite hosted agents can access private repositories in GitHub natively, by authorizing Buildkite to access these GitHub repositories. To access private repositories from another provider, the git-ssh-checkout-buildkite-plugin plugin is available to provide this capability.
To learn more about changes that may need to be completed at an individual pipeline level, see Pipeline migration.
GitHub private repositories
To use a private GitHub repository with Buildkite hosted agents, you need to authorize Buildkite to access your repository. This process can only be performed by Buildkite organization administrators.
- Select Settings in the global navigation to access the Organization Settings page.
- In the Integrations section, select Repository Providers.
- Select the GitHub option.
- Follow the prompts to authorize the services on your GitHub account. You can restrict access to specific repositories during setup.
GitHub access token caching
Buildkite hosted agents provides a feature for temporarily caching access tokens issued by GitHub whenever Buildkite requests one as part of interacting with a private repository. This interaction is established as part of configuring the Buildkite platform as a GitHub App in your GitHub project or organization.
Buildkite caches these GitHub access tokens for 50 minutes, where they remain encrypted on the Buildkite platform. This feature allows your hosted agents to use these GitHub access tokens and avoid hitting your GitHub rate limit, since these tokens can be re-used in subsequent builds.
There's no need to configure this access token caching feature, as it's provided by default as part of Buildkite hosted agents.
Public repositories
Buildkite does not require any special permissions to access public repositories.
Private repositories with other providers
Using Buildkite hosted agents with a private repository on provider other than GitHub, has the following two requirements:
- Add an SSH key as a secret to the Buildkite hosted agent cluster.
- Add the plugin to the initial pipeline steps, and any further steps within the uploaded pipeline.
Add the SSH key secret
Navigate to Agents from the top menu, and open the Cluster for Buildkite hosted agents. In the left-hand side navigation, there will be a Secrets option to follow. Clicking the New Secret button will open a modal to capture the new secret.
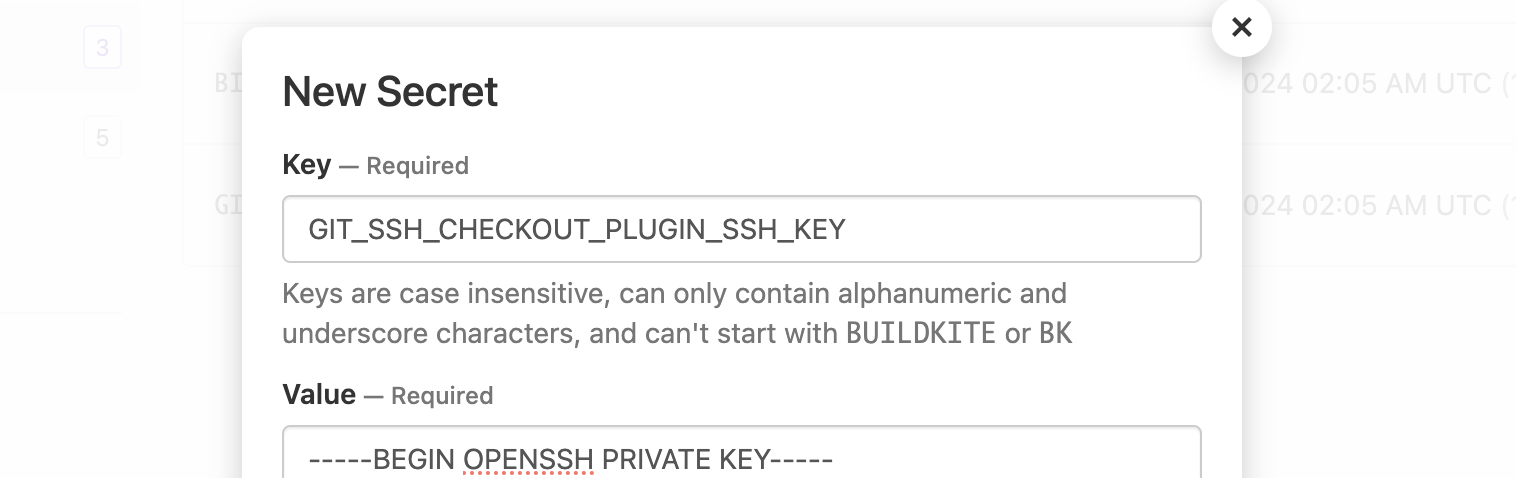
This secret should contain the full private key (including the header and footer) that will be used to access the repository.
If there are multiple distinct keys to be used throughout the cluster, make sure to name them appropriately so they can each be used at their correct times.
Add a new pipeline
With the secret now available, you can add a new pipeline to use it and access the Git repository.
The availability of the secret allows the creation of a new pipeline to utilize it and access the Git repository.
Once the secret is available, a new pipeline can be set up to use it and enable Git repository access.
Create a new pipeline following the Create a new pipeline without provider integration link on the New pipeline page. Complete the form with the basic details about the new pipeline, including the Git URL. At this time, the Steps can also be updated to include the plugin usage.
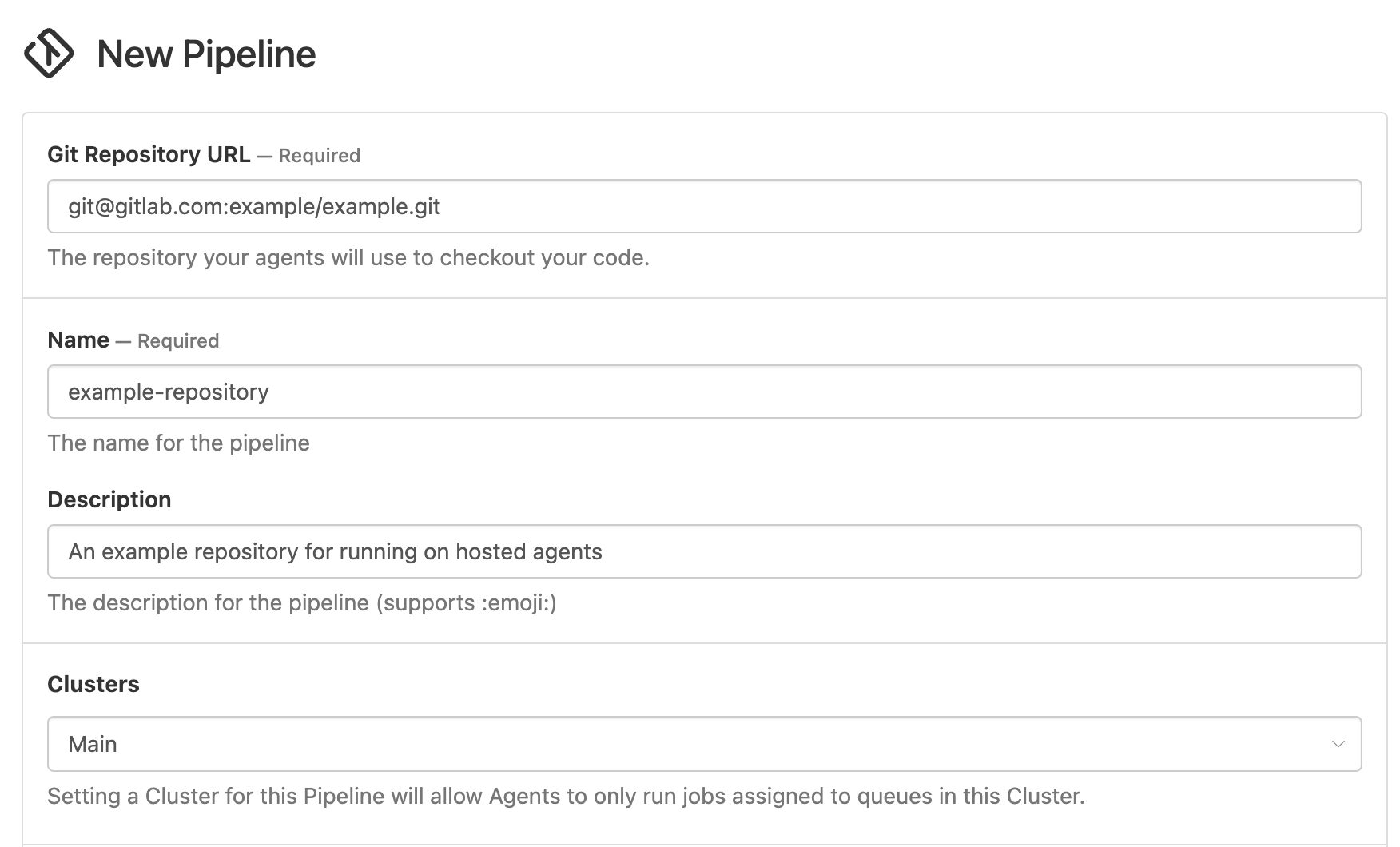
To illustrate an example, if we assume a secret named GIT_SSH_CHECKOUT_PLUGIN_SSH_KEY now exists we can set our Steps value accordingly.
steps:
- label: ":pipeline: Upload"
command: "buildkite-agent pipeline upload"
plugins:
- git-ssh-checkout#v0.4.1:
This base step content uses the new plugin with the default values to complete the Git checkout.
Once created, a screen is presented about setting up Webhooks. If the Git provider being used supports the GitHub format of webhook communication, the details shown can be used to complete the integration. If not, you can use the Skip Webhook Setup button to skip this step. This will mean that builds will require manual triggering.
At the completion of the pipeline creation process, a build can now be triggered that will use the SSH key from the secret to clone the Git repository.