- Resources
- /
- Changelog
C# support for the Buildkite SDK
The Buildkite SDK now supports C#, starting in v0.8.0. You can define and manage your Buildkite pipelines programmatically in C#, with the same type-safe experience available in the SDK's other supported languages: JavaScript/TypeScript, Python, Go, and Ruby. The package is now available for download from NuGet.
Pete
GCP and Azure support across popular plugins
Several of our most popular plugins now support GCP and Azure, making it easier to use Buildkite with your preferred cloud provider.
The secrets plugin fetches secrets and injects them as environment variables into your builds. It now supports GCP Secret Manager and Azure Key Vault, in addition to Buildkite Secrets.
The cache plugin stores and restores build cache between pipeline runs. It now supports Google Cloud Storage and Azure Blob Storage backends alongside Amazon S3.
The docker-cache plugin speeds up Docker builds by caching images between pipeline runs. It now supports Azure Container Registry as a caching provider.
The docker-image-push plugin builds and pushes Docker images to Google Artifact Registry and Azure Container Registry alongside its existing support for Amazon ECR and Docker Hub.
(New) The azure-login plugin authenticates your Buildkite agents with Azure using managed identity or service principal credentials. Pair it with our secrets, docker-image-push, or cache plugins to streamline your Azure workflows.
Pete
API access tokens now support expiry dates
You can now set an expiry date when creating an API access token. Once a token expires, any API requests using it will stop working, so forgotten tokens don't become a security risk.
Choose from preset durations (1 day, 7 days, 30 days, 90 days, 1 year), pick a custom date, or select "Never" to create a token with no expiry.
Key details
- Expiry is set at creation and cannot be changed afterward. To extend access, create a new token.
- You'll receive an email 3 days before a token expires, with a link to create a replacement.
- Expired tokens are automatically deleted after a grace period.
- All existing tokens are unaffected and continue to work with no expiry.
For more information, see the API access tokens documentation.
Himal
Test Engine Client (bktec) v2.1.0: Custom test runner, split slow files by example, and tag filters for pytest
Test Engine Client (bktec) v2.1.0 introduces a new custom test runner and several improvements for pytest users.
🛠️ Custom test runner
You can now use bktec to split tests with any test runner that supports running specific test files via command-line arguments. For details, see the custom test runner documentation for Test Engine Client.
🐢 Split slow files by example (pytest)
You can now split slow test files by individual test examples when using pytest. This helps distribute long-running tests more evenly across agents and reduces build times.
🏷️ Tag filters (pytest)
The new --tag-filters option allows you to select and run tests based on a single key:value tag pair when using pytest.
Example:
bktec run --test-runner pytest --tag-filters "test.type:integration"Read more about splitting slow files by example and tag filters in the Test Engine Client pytest documentation.
Naufan
CircleCI Translation in Pipeline Conversion Tool
You can now bring your CircleCI pipelines over to Buildkite even faster! Our pipeline conversion tool now supports more cases to convert CircleCI workflows to Buildkite pipelines. In addition to generating pipeline YAML that you can run, the output also includes information about required agent setup and other adjustments that may be needed to get a complete functional pipeline.
This makes it simple to:
- Copy an existing CircleCI pipeline
- Instantly see the equivalent Buildkite pipeline steps
- Speed up trying out Buildkite with less manual rewriting
👉 Try it out in the Pipeline Converter
📖 See the documentation
Owen
Step state now includes canceled for canceled steps
Steps that were canceled (either directly or as part of a canceled build) now return state: "canceled" in the REST API and webhooks, instead of state: "finished" with outcome: "errored".
Previously, canceled steps were grouped with timed-out and expired steps under the same errored outcome. This made it difficult to distinguish between steps that were manually canceled versus those that failed due to timeouts or system errors.
With this change:
- Canceled steps:
state: "canceled",outcome: "neutral" - Timed-out/expired steps:
state: "finished",outcome: "errored"
If you have integrations that parse step state from webhooks or the REST API, update your logic to handle the new canceled state:
- if step.state == "finished" && step.outcome == "errored"
- # Could be canceled, timed out, or expired
+ if step.state == "canceled"
+ # Step was canceled
+ elsif step.state == "finished" && step.outcome == "errored"
+ # Step timed out or expiredThis affects step.finished webhook events and REST API endpoints that return step data.
Sarah
GitHub Actions Translation in Pipeline Conversion Tool
You can now bring your GitHub Actions workflows over to Buildkite even faster! Our pipeline conversion tool now uses AI to translate Actions workflows to Buildkite pipelines. In addition to generating pipeline YAML that you can run, the output also includes information about required agent setup and other adjustments that may be needed to get a complete functional pipeline.
This makes it simple to:
- Copy an existing Actions workflow
- Instantly see the equivalent Buildkite pipeline steps
- Speed up trying out Buildkite with less manual rewriting
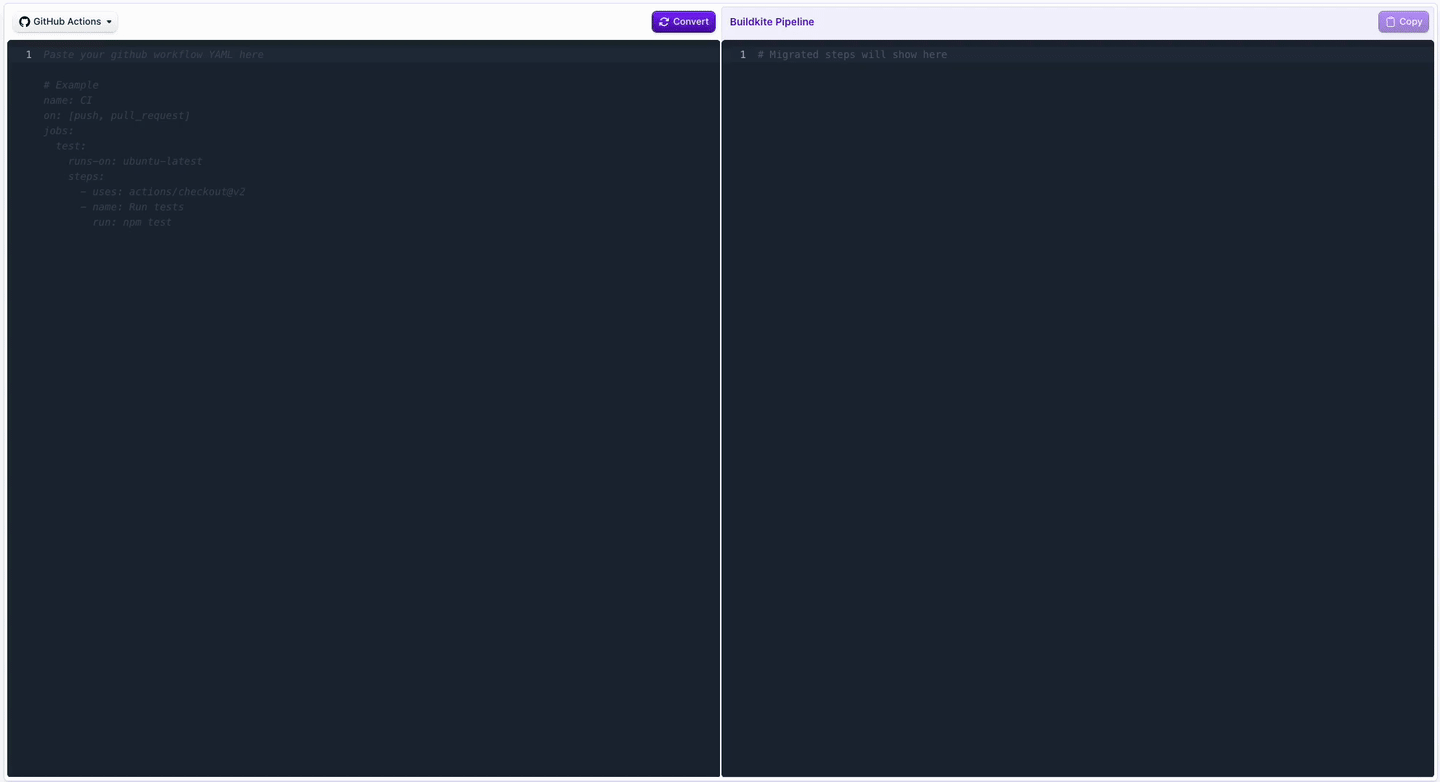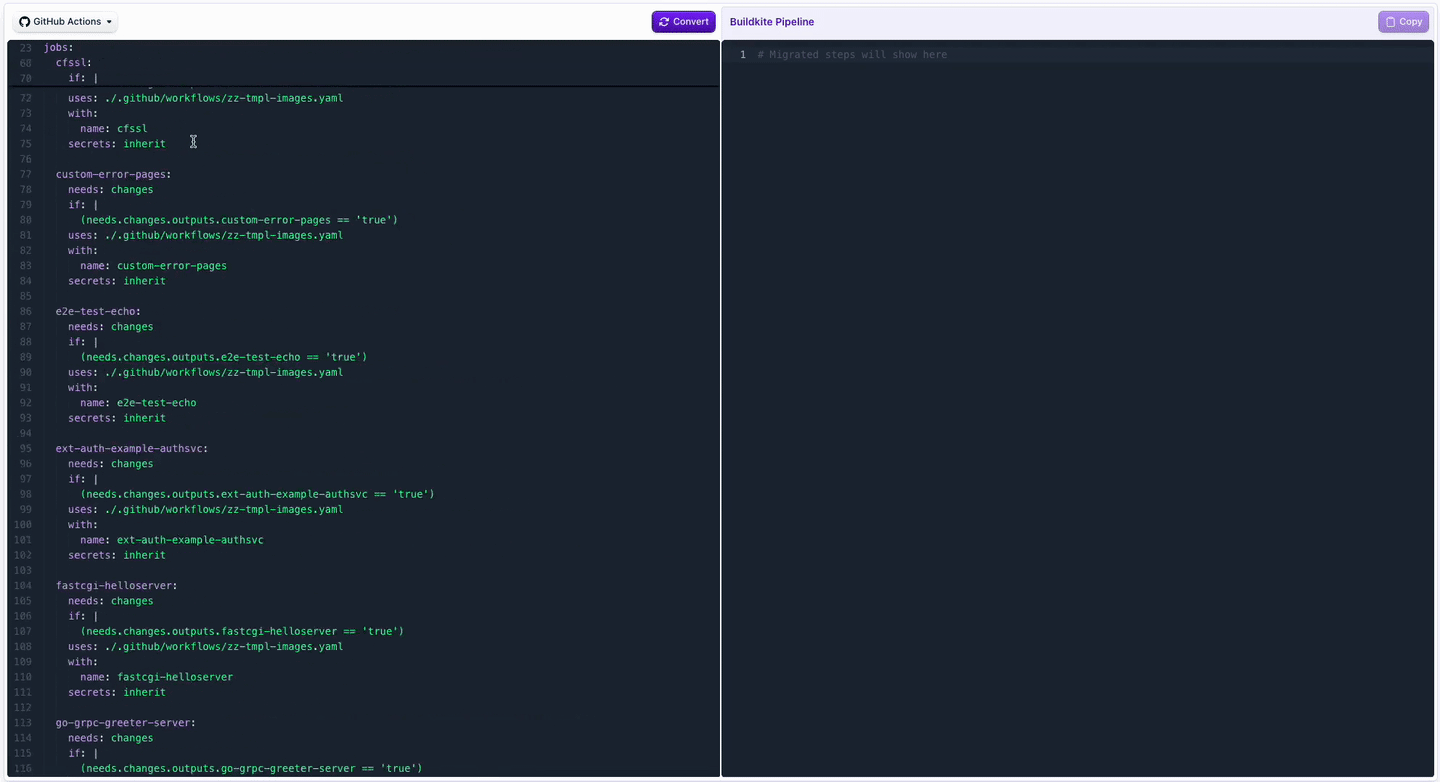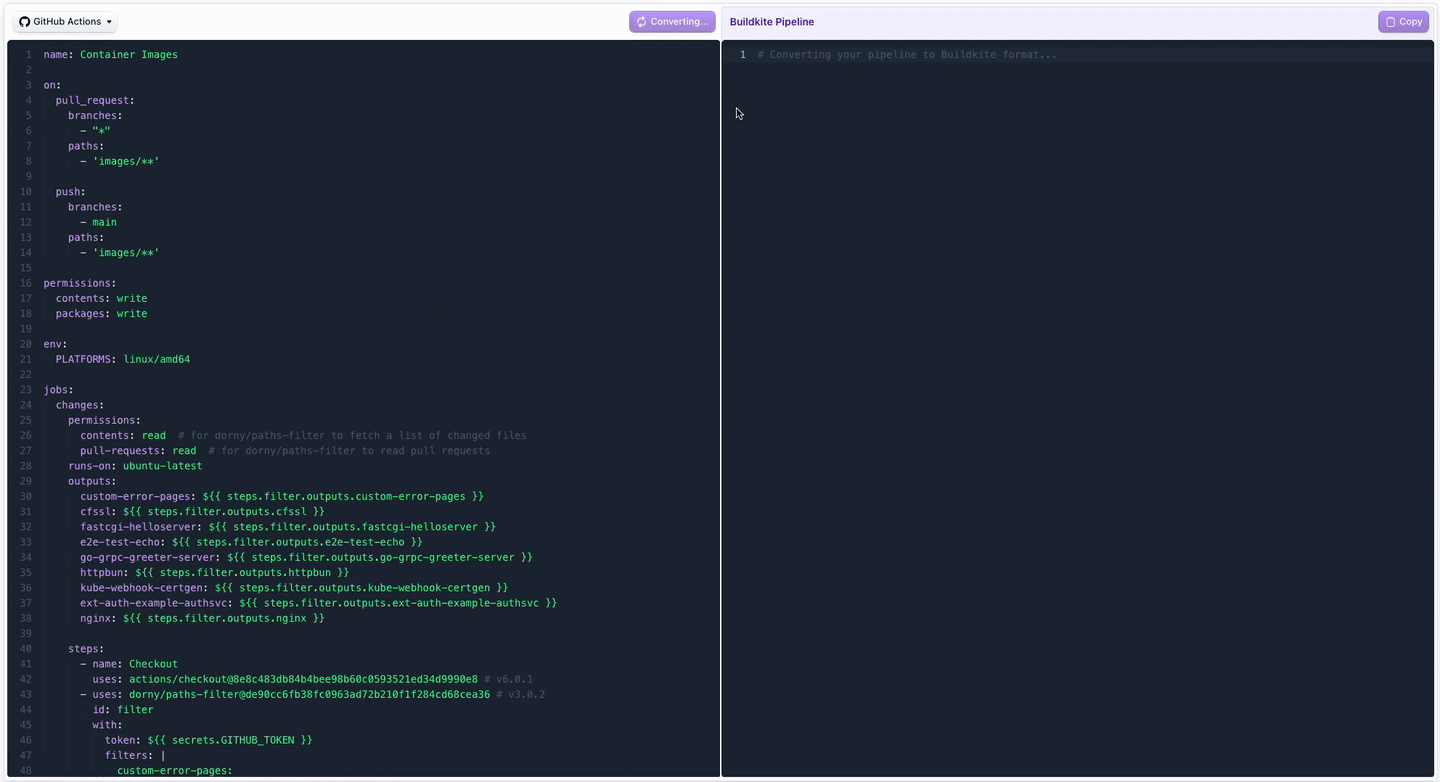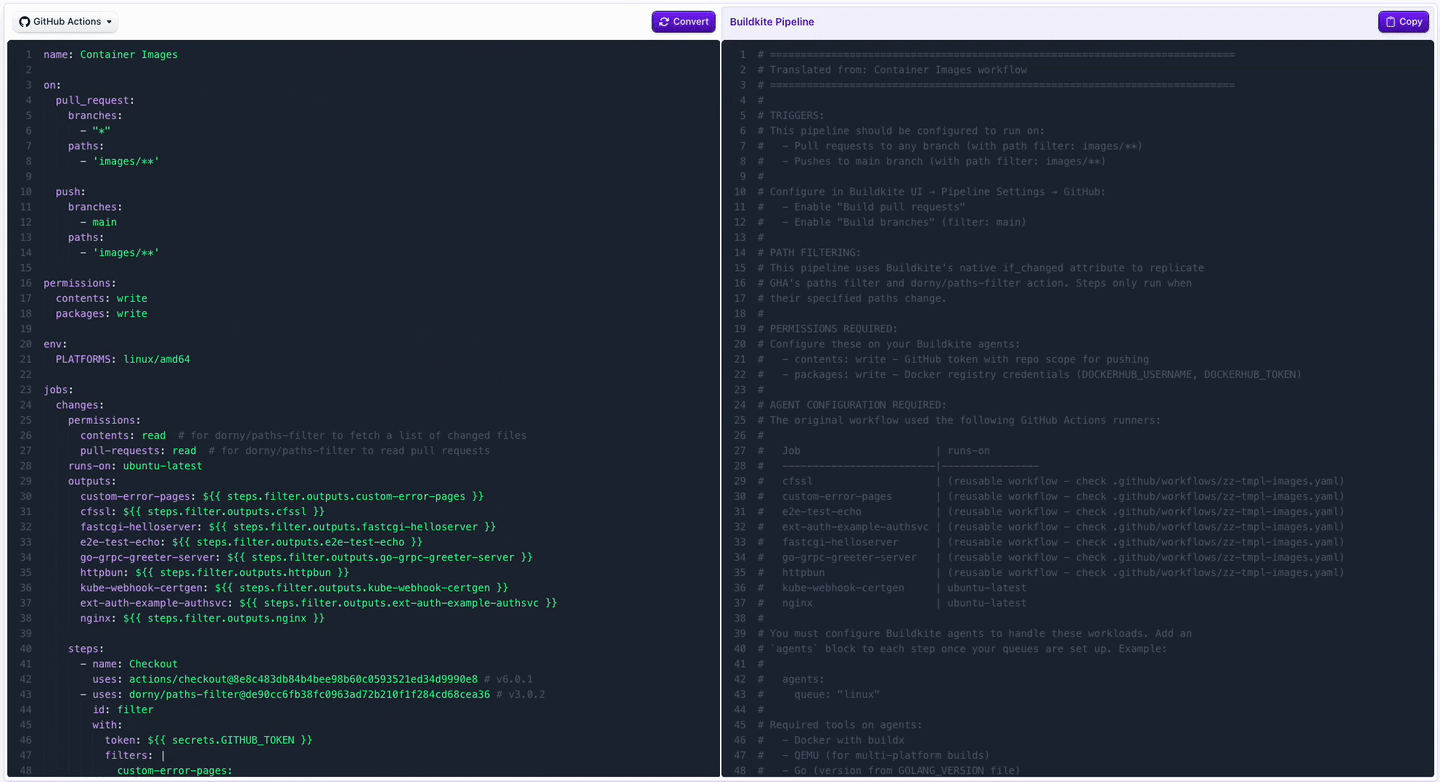
👉 Try it out in the Pipeline Converter
📖 See the documentation
Owen
Multi-line selection in job logs
You can now select multiple log lines by Shift+Clicking, making it easier to copy multiple lines or share a permalink to a line range.
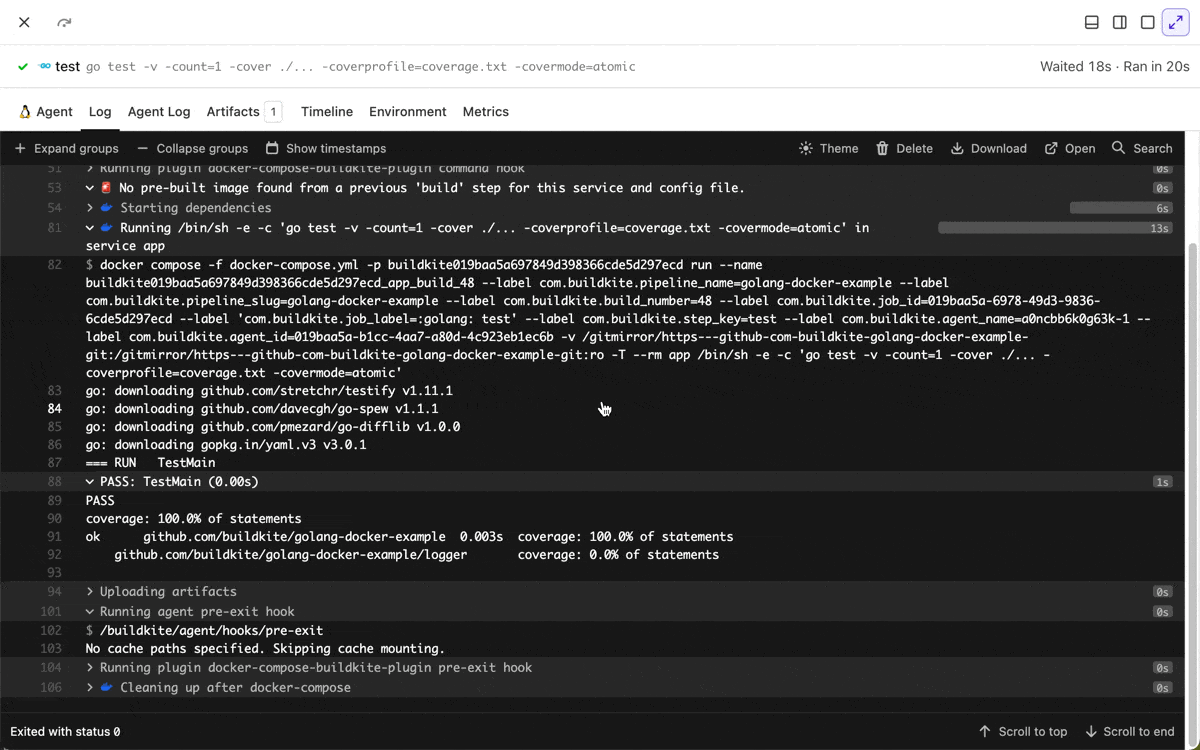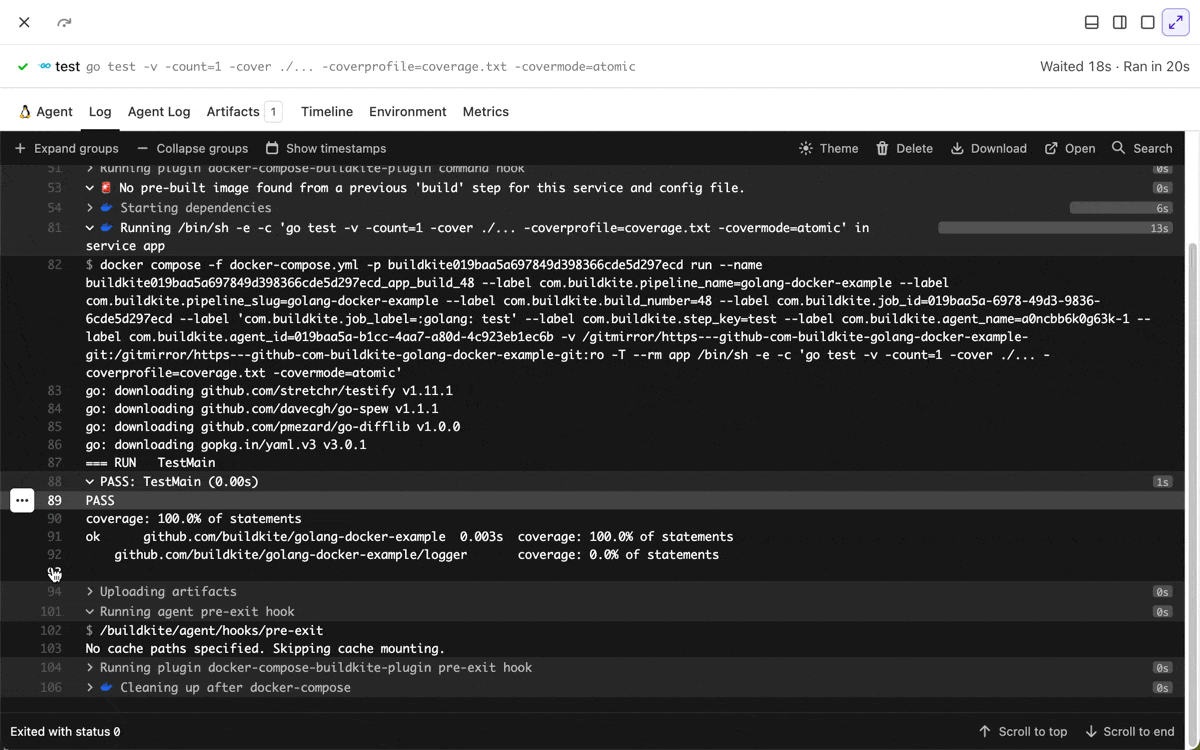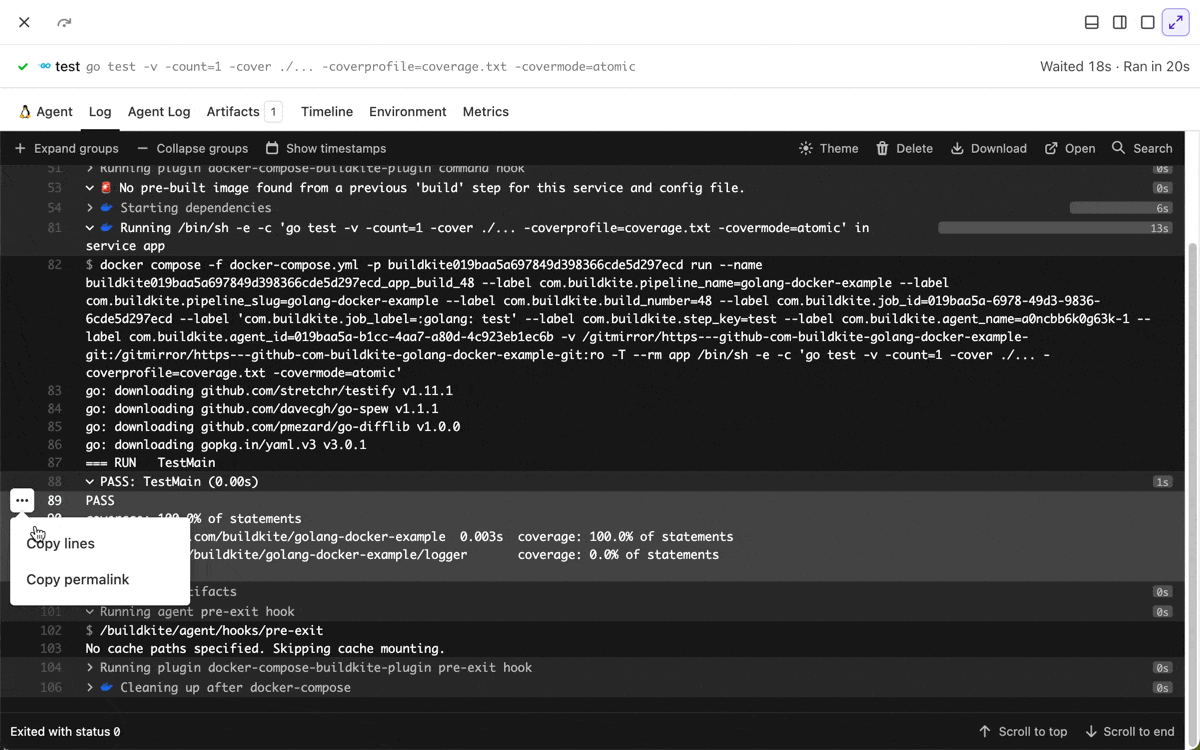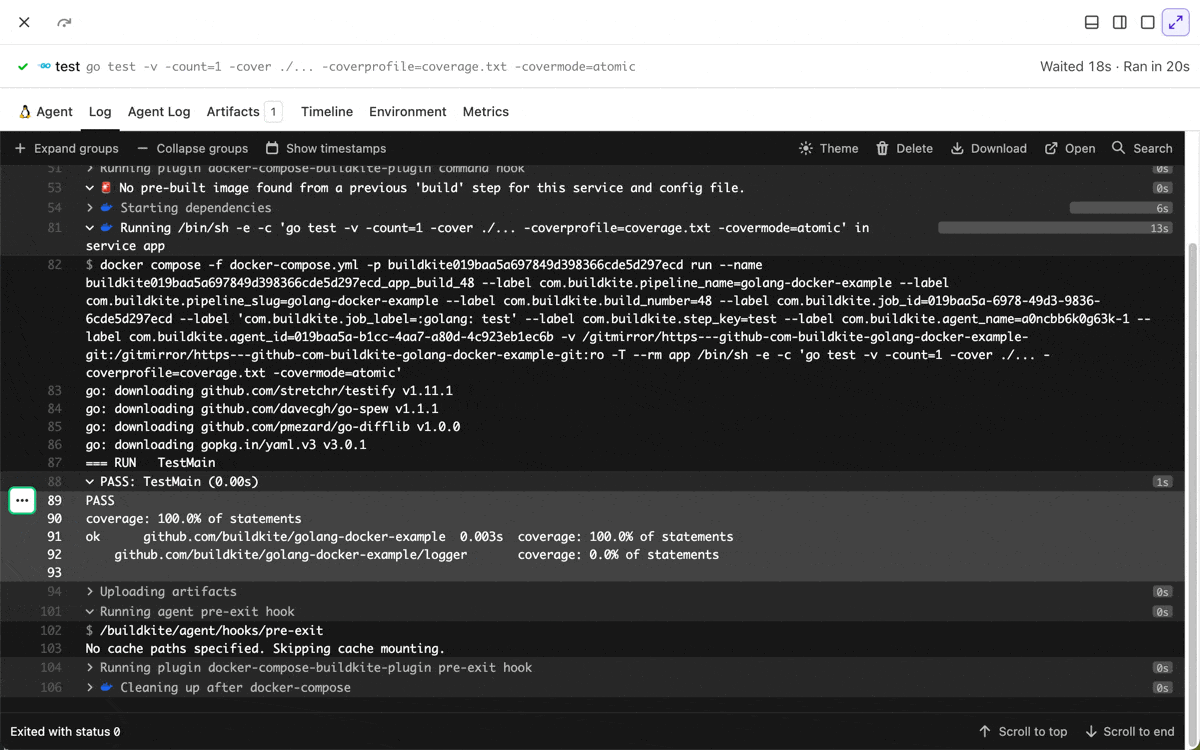
Chris
Suite summary view customization
Teams can now customize their suite summary view to better track the trends that matter most. Save default filters and show or hide metric charts to tailor the view to the suite insights you care about.
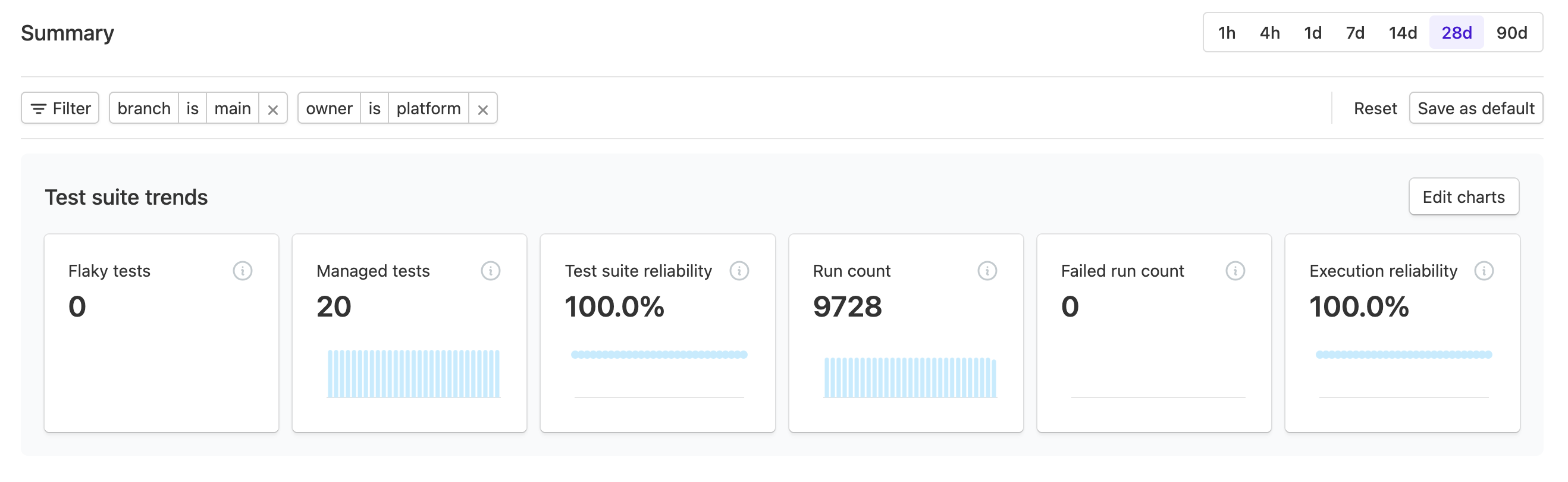
This makes it easier for your team to:
- Focus on the most relevant suite trends
- Reduce visual noise by hiding unused metrics
- Keep a consistent, shared view across your team
Meghan
Elastic CI Stack for GCP now available (Preview)
We're excited to announce that our Terraform module for the Elastic CI Stack for GCP is now in Preview! The included Terraform modules will enable you to deploy and manage autoscaling Buildkite agent clusters in GCP with ease.
This Terraform project supports the following basic features:
- Autoscaling based on agent utilization metrics
- Support for both Linux agents on both x86-64 and ARM64 architectures
- Built-in secrets management via GCP Secrets Manager
The module is currently in preview. If you encounter any issues or have feedback, please raise an issue on GitHub or reach out to support@buildkite.com.
Check out GCP Elastic CI Stack in our docs, the module's GitHub repository, and our example configurations to get started.
Owen
New incident plugins released
We've just released two new incident management plugins that allow you to integrate your Buildkite pipelines with PagerDuty and Incident.io.
PagerDuty plugin
The PagerDuty plugin can be configured to check the status of a single job, or an entire build. If the job or build fails, the plugin will create a PagerDuty incident of whatever severity you specify.
Incident.io plugin
The Incident.io plugin can be configured to check the status of a job. Like the PagerDuty plugin, it will create an incident if the job fails. The Incident.io plugin accepts any of the custom severity levels you may have defined in Incident.io, and can optionally fill out the incident name and summary for you, as well as specify whether the incident Slack channel should be public or private.
Follow the links above for complete usage information for each of these plugins. Have questions or need help? Reach out to us at support@buildkite.com.
Owen
bktec v2.0.0 - now with dynamic parallelism
We have released a new major version of the Buildkite test engine client (bktec).
This version introduces dynamic parallelism, intended to accommodate builds where the number of tests run is variable, for example when predictive test selection is used.
From v2.0.0 bktec can dynamically set command step parallelism to achieve a specified target build duration.
📚 Learn more about bktec dynamic parallelism.
Note on upgrading to bktec v2.x.x sub-command support has been added in this release.
Calling bktec without a sub-command is no longer supported, so when upgrading to v2.x.x please update your step definitions.
# < v2.0.0
command: bktec
# >= v2.0.0
command: bktec runMalcolm
Display properties customization
You can now toggle display properties in your test data tables. Turn on/off fields like State, Location, Repository, and Labels so you only surface the context that’s relevant to you and clear out any extra clutter.
Customizable display properties are available in:
- The Tests tab for a build or a build's job
- The Tests view and when viewing saved views in Test Engine
- The single run view in Test Engine
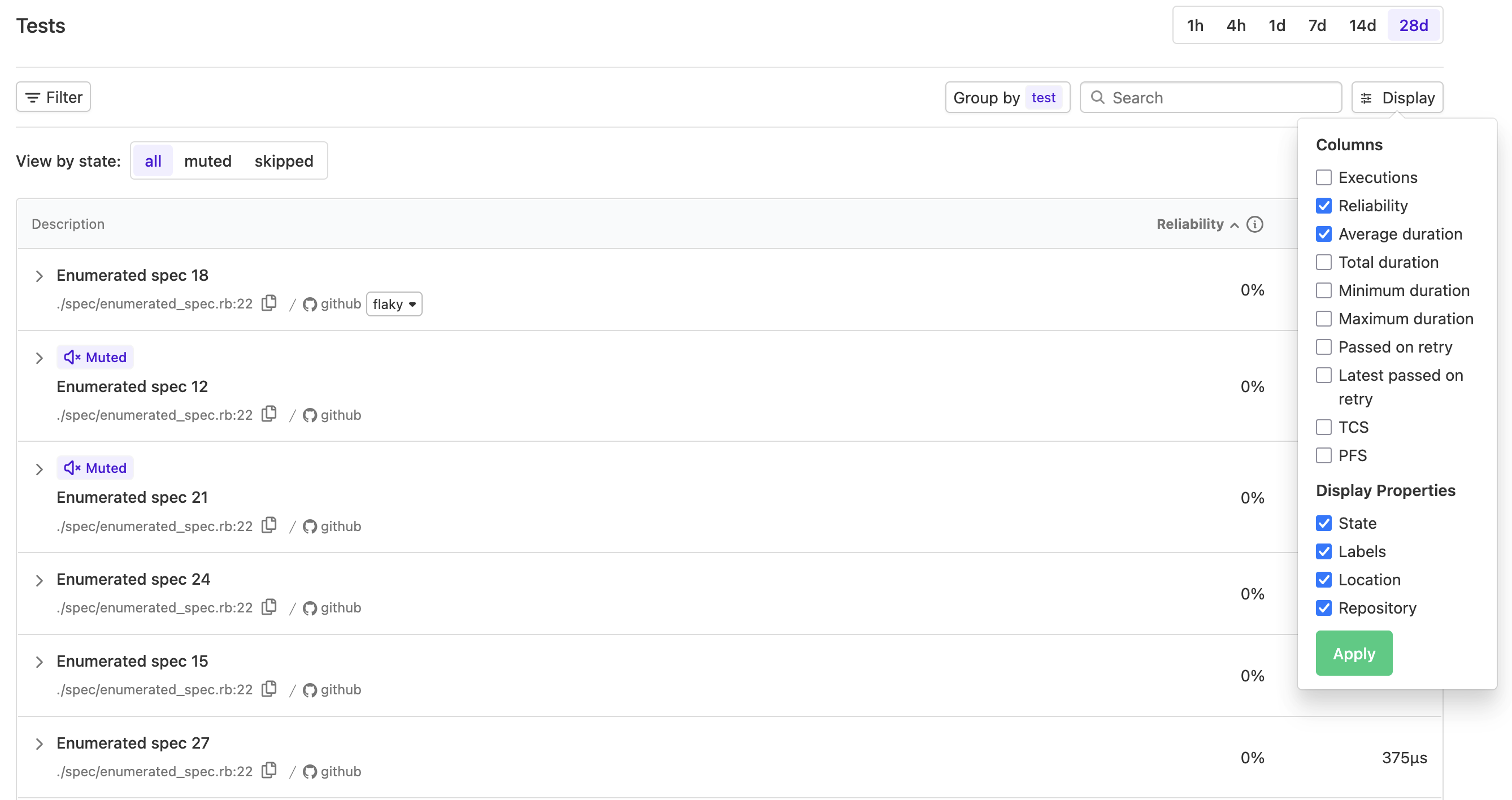
Saved views have also been updated, allowing your selected display properties to be stored as part of the saved view configuration. This ensures your preferred layout is preserved and shared across your suite.
Meghan
Control where your retries run with Retry Agent Affinity
A common frustration when running in CI is that agent instances can become corrupted in such a way where they are no longer able to consistently run jobs. This can lead to retries failing, which can be difficult to diagnose and fix. Within Buildkite, by default, jobs are run on the agent that has most recently finished a job, which can lead to retries running on the same agent that failed the first time causing repeated failures.
With the new Retry Agent Affinity feature, you can control where your retries run. Retry agent affinity is set at the Cluster Queue level, and when set to prefer-different, will prefer to run retries on a different agent than the one that failed the first time. This can help to avoid retries failing due to repeated runs on the same corrupted agent.
To set the Retry Agent Affinity on a cluster queue, you can go into the Cluster Queue settings and select the Retry Agent Affinity option:
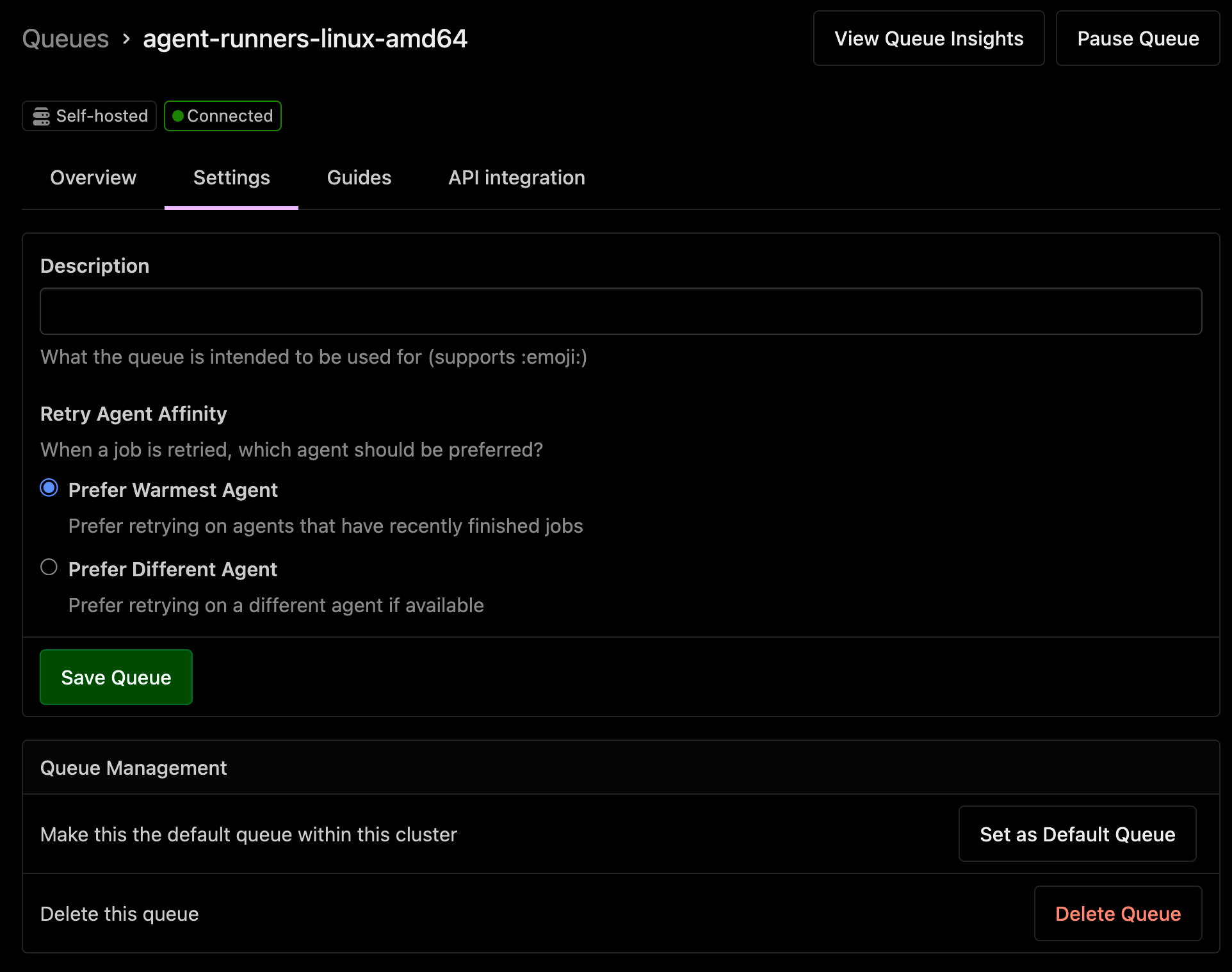
Alternatively, this value can be set via both the REST and graphQL APIs.
Availability
Retry agent affinity is available for all self-hosted cluster queues.
If your agents are using an acquire-job workflow such as agent-stack-k8s, the setting will have no effect, as Buildkite doesn't control job dispatch for these agents.
Retry agent affinity can't be set on hosted queues, as agents in hosted queues are ephemeral, and so retries will always run on different agents from the original job.
Benno
New Test monitor for Test Engine Workflows
You can now detect and manage newly introduced tests with the New Test monitor in Test Engine Workflows!
The New Test monitor automatically detects newly introduced tests to your test suite. By triggering appropriate actions to track and validate the performance of new tests, you can proactively manage these new tests and ensure you're not introducing flaky tests into your test suite.
What's new
- Detect newly introduced tests in your test suite automatically
- Full workflow action support including labeling, state management, Slack notifications, and Linear issue tracking
- Tag-based filtering to trigger actions only for new tests with specific tags
Learn more about the New Test monitor in our documentation.
Naufan
Group executions by location and tag
We're excited to announce that test executions can now be grouped by location and tag! Grouping executions makes it easier to compare related tests side-by-side, helping you quickly spot patterns, outliers, and performance differences. This is especially useful for teams that use tags to classify tests by component, owner, type, cloud provider, or any other custom metadata.
The new grouping functionality is available in three areas of the platform:
- In the Tests tab for a build or a build's job (shown below)
- In the Tests view and when viewing saved views in Test Engine
- When viewing a particular run in Test Engine
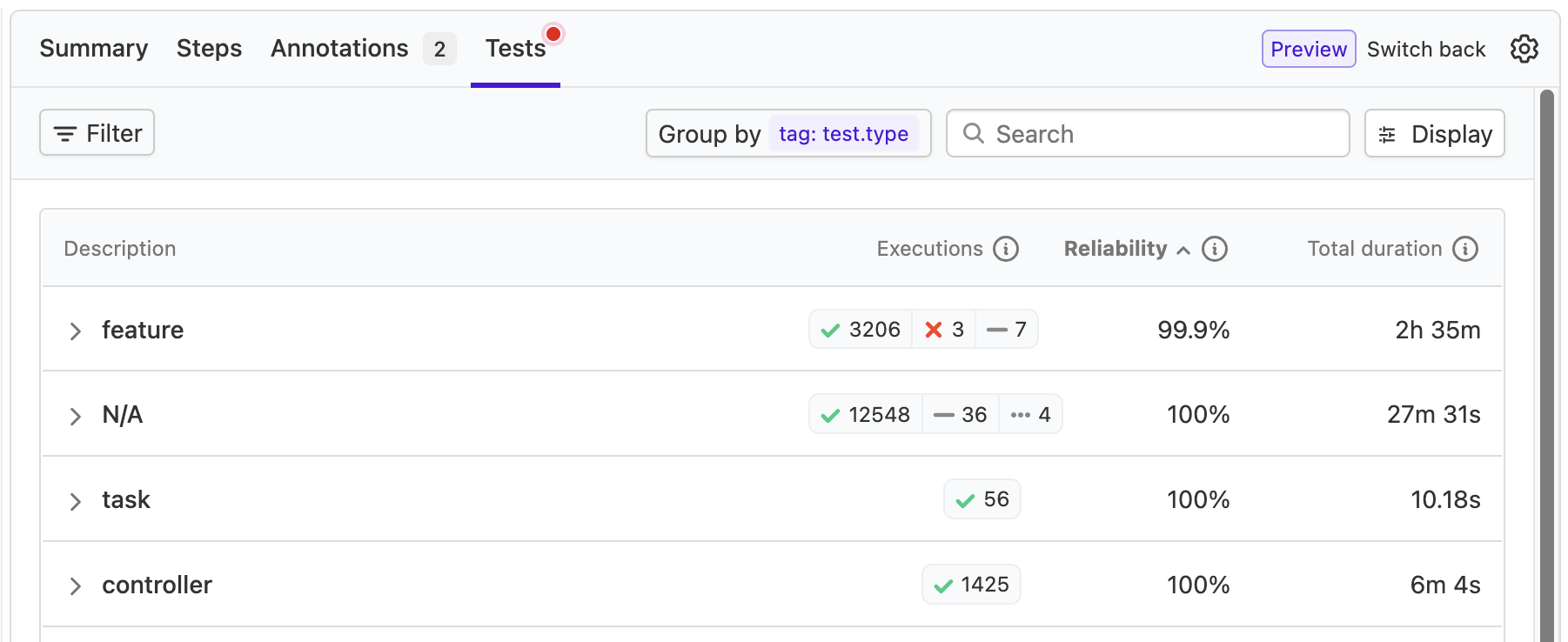
If you're not currently collecting tag metadata for your test executions, read the docs to learn more.
Steve
Elastic CI Stack for AWS now available as a Terraform module (Preview)
We're excited to announce our Terraform module for the Elastic CI Stack for AWS is now in Preview!
For teams who prefer infrastructure-as-code with Terraform over CloudFormation, you can now deploy and manage your autoscaling Buildkite agent clusters using familiar Terraform workflows.
This Terraform module supports all the features available in our Elastic CI Stack for AWS:
- Autoscaling based on agent utilization metrics
- Support for both Linux and Windows agents
- Configurable spot and on-demand instances
- Built-in secrets management via S3 and AWS Secrets Manager
- Pipeline signing with KMS
- Scheduled scaling for cost optimization
The module is currently in preview. If you encounter any issues or have feedback, please raise an issue on GitHub or reach out to support@buildkite.com.
Check out Setup with Terraform in our docs, the module's GitHub repository, and our example configurations to get started.
For those who prefer CloudFormation, the Elastic CI Stack for AWS is also available as a CloudFormation Stack.
Joe
New golangci-lint plugin released
Running golangci-lint is now even simpler, with the release of the golangci-lint plugin for linting and formating Go code in your CI/CD pipeline.
The plugin makes it easy to integrate Go code quality checks into your Buildkite pipelines with minimal configuration. It runs golangci-lint using Docker by default, but can also use a local binary if preferred.
Basic usage
Add the plugin to your pipeline with minimal configuration:
steps:
- label: "Go Lint"
plugins:
- golangci-lint#v1.0.0: ~For complete documentation and all available options, see the golangci-lint plugin.
Ben
New deployment plugins released
We're happy to announce that we have developed three new plugins that enable easy deployments and rollbacks using several popular code deployment tools.
The AWS Lambda Deploy plugin supports AWS Lambda deployments and rollbacks. It can deploy both zip files and container images, and uses aliases to enable blue/green deployments. Optional features include automatic rollback in case of failure, and a customizable health check for verifying the deployment. The plugin will also create detailed build annotations about the deployment and rollback process, for post-build review.
The ArgoCD Deployment plugin supports ArgoCD deployments and rollbacks. It leverages the ArgoCD API to perform health checks after the deployment is complete, and collects application and pod logs to upload as build artifacts for later review. It also includes support for sending your team Slack notifications when appropriate, as well as customizable manual rollback workflows.
The Deployment Helm Chart plugin supports simple deployments and rollback workflows using Helm. Specify your chart, release name, namespace, and optional values, and the plugin will take care of the rest. Rollbacks can be triggered by a user after manual application health checks.
Follow the links above for complete usage information for each of these plugins. Have questions or need help? Reach out to us at support@buildkite.com
Owen
Jenkins Pipeline Translation in Migration Tool
You can now bring your Jenkins pipelines over to Buildkite even faster! Our migrate tool now supports pasting in your declarative or Groovy Jenkinsfile and will automatically translate it into Buildkite steps.
This makes it simple to:
- Copy an existing Jenkins pipeline
- Instantly see the equivalent Buildkite pipeline steps
- Speed up migrations with less manual rewriting
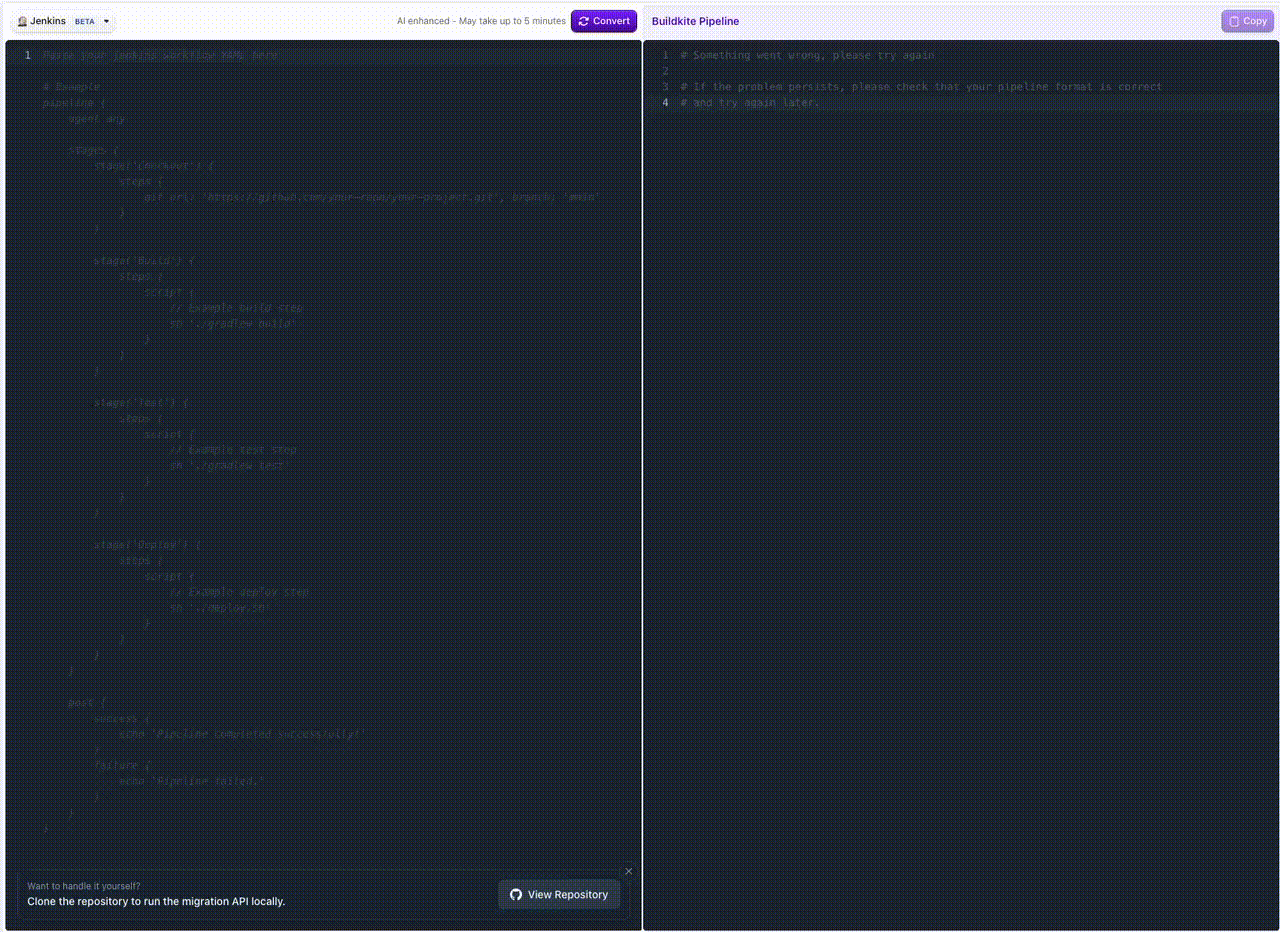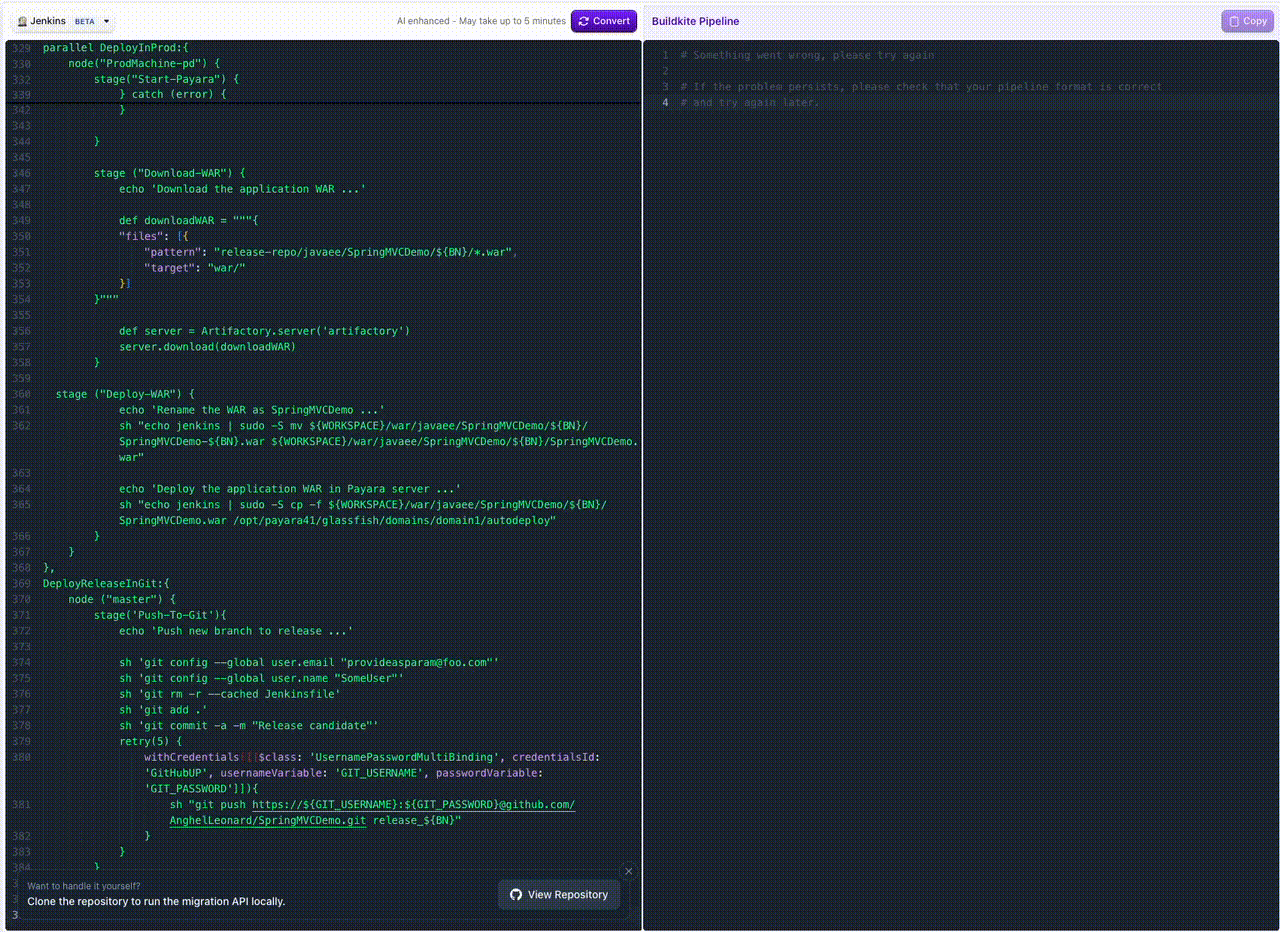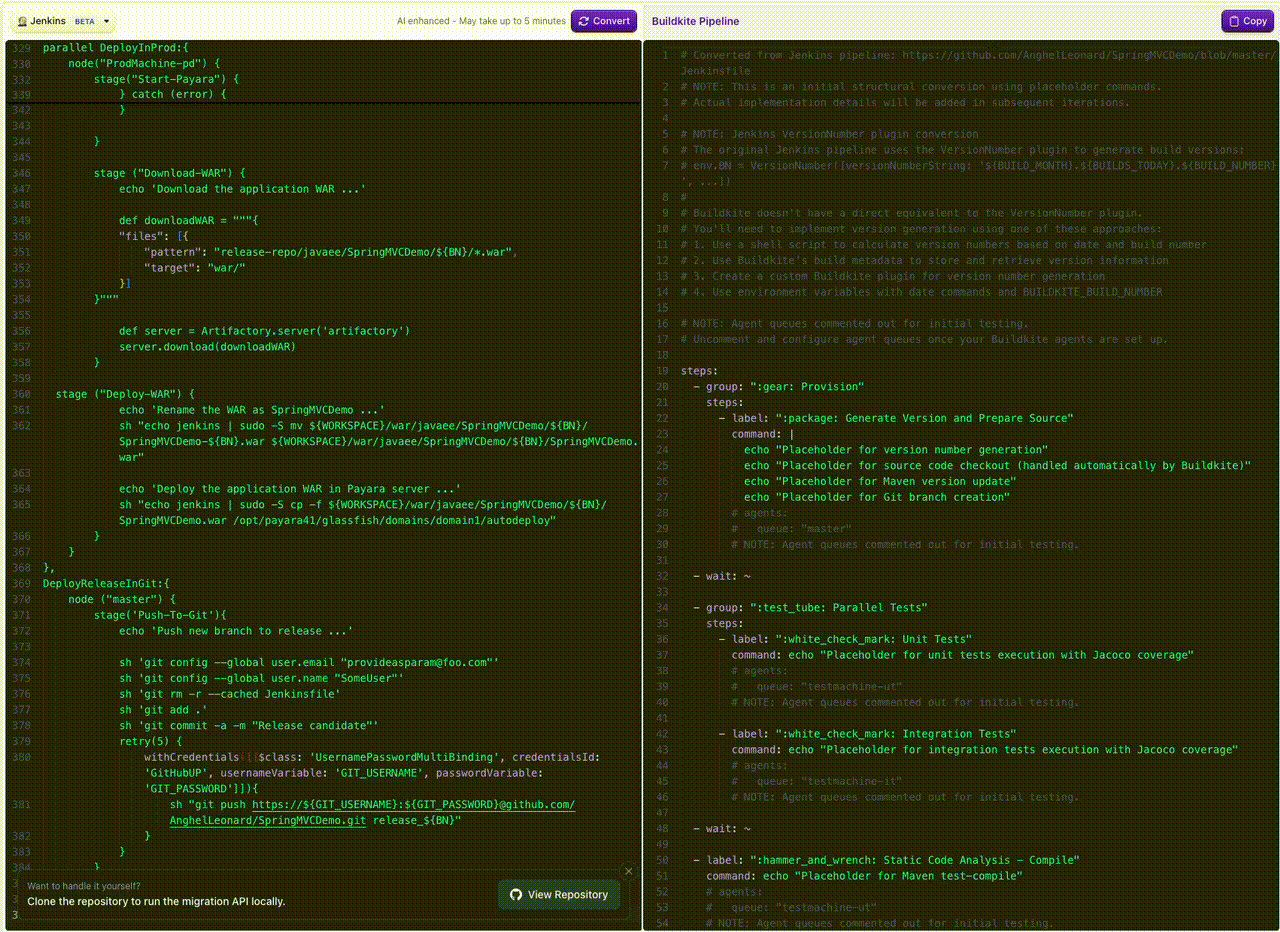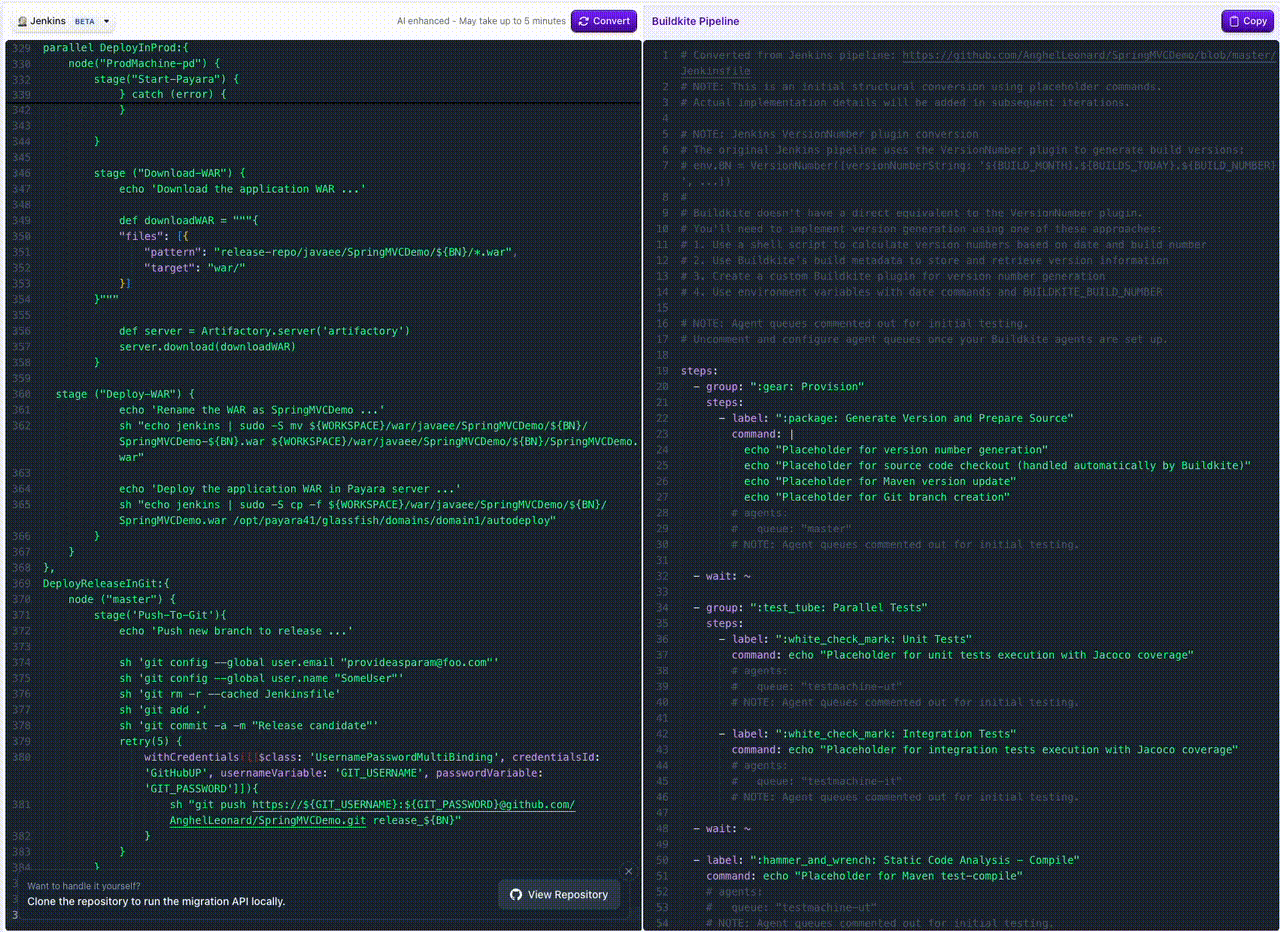
👉 Try it out in the Migrate Tool
📖 See the documentation
Ben
Start turning complexity into an advantage
Create an account to get started for free.