At Buildkite, we believe development teams should be free to choose best-of-breed tools that fit their processes and tech stacks. We designed Buildkite Pipelines to be an open, extensible CI/CD platform to support exactly that—integrate third-party tools with a powerful, lightweight plugin system.
Let's be real, though. Today's release cadences are enough to make a developer's head spin. To keep up, teams often lean on third-party code dependencies. But with that convenience comes risk. An insecure package here, a vulnerable library there, and before you know it, you're playing whack-a-mole with security holes (and we know that never ends well).
This tension between speed and security led to the rise of DevSecOps. By embedding security practices and tooling directly into delivery pipelines, you can spot issues early, prioritize the biggest fires, and fix them before shipping to production. But this way of working relies on your CI/CD platform being flexible enough to move with the times and integrate with leading DevSecOps solutions.
That's why we're excited to announce Buildkite's new integration with Lacework, the data-driven cloud security platform. This integration allows teams to improve security practices through CI/CD pipelines without sacrificing velocity.
The rise of DevSecOps
Over the last decade or so, the workload for security teams has steadily increased. One way teams started to manage this was to partner more closely with development teams.
Enter DevSecOps—looping security into the entire development cycle from the beginning instead of treating it like an afterthought. By embedding security tools, scans, and risk reporting directly into delivery pipelines, teams could identify and resolve issues during the build process before they snowballed into production crises.
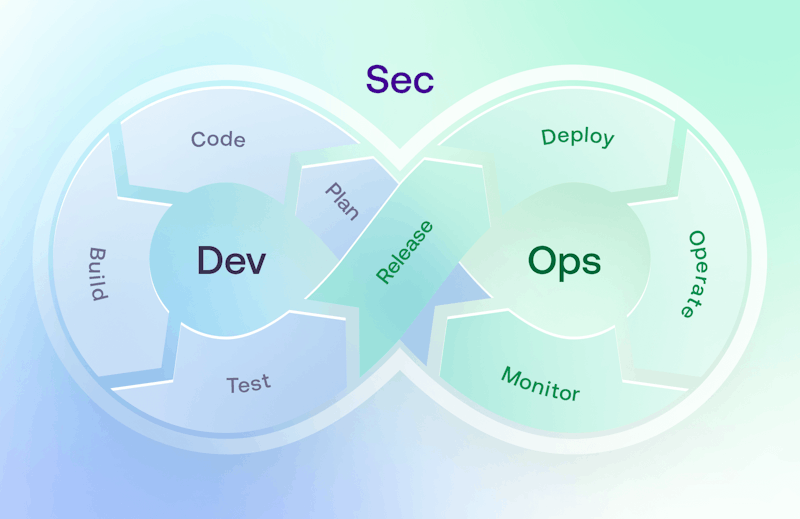
DevSecOps loop
The benefits are clear:
- No more slamming on the breaks for security fire drills at the 11th hour.
- Real-time visibility into your security posture across the full software development lifecycle.
- Ability to prioritize and remediate risks based on how critical they are.
- Seamless governance without sacrificing delivery speed.
In short, following DevSecOps practices helps security teams enable developer velocity. Of course, pulling this off requires some key ingredients, including a flexible CI/CD platform and security expertise, which is exactly what Buildkite's integration with Lacework provides.
Introducing the Lacework plugin
Lacework is a cloud-native application protection platform (CNAPP) that helps you improve the visibility of risks throughout the software development lifecycle.
With Lacework, you can:
- Run SCA: Run software composition analysis (SCA) across all code components (proprietary, open source, and third-party dependencies) to identify vulnerabilities and licensing risks.
- Scan IaC: Assess Terraform, CloudFormation, Kubernetes manifests, and other infrastructure-as-code (IaC) tooling to remediate misconfiguration risks.
- Scan containers: Analyze container images to detect misconfigurations and embedded vulnerabilities.
- Run SAST: Run highly scalable and accurate static application security testing (SAST) across your codebase.
Adding Lacework to your pipelines lets you embed security guardrails without disrupting developer velocity, securing your entire cloud from one place.
SCA: Gain control of your software supply chain
In the era of "move fast and break things," it's not surprising that many teams rely on third-party code. Why reinvent the wheel when you can npm install your way to lightning-fast feature delivery? But every one of those external dependencies is a potential unknown in your app's security posture. That's where software composition analysis (SCA) comes in.
SCA provides a comprehensive inventory of all code components within your applications. It identifies known vulnerabilities and licenses associated with open-source and third-party libraries. This allows you to evaluate risk exposure and remediate issues before they can be exploited.
Lacework's SCA capability helps you:
- Identify all third-party code dependencies.
- Automatically prioritize and remediate associated vulnerabilities.
- Detect risk and non-compliance associated with open-source licenses.
You also get a comprehensive view of your software supply chain through the generated software bill of materials (SBOM).
IaC security: Secure cloud infrastructure before deployment
In the old days, spinning up a server meant physically racking and stacking hardware in a dusty data center. But in the age of the cloud, infrastructure is just code. A few lines of Terraform or CloudFormation, and boom—you've got a fully-provisioned environment ready to go.
While infrastructure-as-code (IaC) has been a game-changer for automating deployments at scale, it's also opened up a new frontier for potential security issues. If there is one little misconfiguration in your IaC templates, you might inadvertently leave your cloud assets more exposed.
But worry not. Lacework solves that problem with its IaC security scanning capabilities. By integrating its scanners directly into your Buildkite pipelines, you can automatically audit your IaC files for misconfigurations and compliance issues before they manifest in your live cloud environments.
Comprehensive container security
Containers have taken the development world by storm, revolutionizing how to build and ship portable software. But they come with their own risks. Containers are like nested dolls of code—they've got layers on layers of dependencies, from the application itself down to the underlying operating system. And each one of those layers is a potential hiding spot for security holes.
Lacework's container scanning helps you find and address vulnerabilities before they reach production. It cross-references your container images against a massive database of known CVEs and best-practice security policies, flags any issues, and provides prioritized remediation advice based on the severity of the risk.
SAST: Shift security left
Static application security testing (SAST) scans your source code to find any potential security flaws before they make it into the wild. Some SAST tools have a history of being slow and producing unreliable results, but Lacework makes code scans fast and accurate.
With Lacework SAST, you get:
- Detection of most OWASP vulnerabilities.
- Smart prioritization of findings based on risk severity and exploit likelihood.
- Fast scans that can process millions of lines of code in minutes.
Because Lacework's SAST integrates with its broader platform, you get a unified view of your application security posture across your codebase, dependencies, and infrastructure—no more siloed tools or piecing together scattered reports.
How to get started with the Lacework plugin
You can start using these Lacework features by setting up the prerequisites and including the Lacework plugin in your pipeline definitions.
Prerequisites:
- A Lacework account. If you don’t have an account, sign up to start a free trial.
- Install the Lacework CLI on the agent. The CLI sends the metadata schema to Lacework so you can view the output in the Lacework UI.
- Install the components you want to use in Lacework:
- Make your API key and secret available to the job using a secret manager or environment hook. To get the values for these secrets, follow the instructions to create a Lacework API key.
- Know your Lacework account name. If your login URL is
mycompany.lacework.net, your account name ismycompany.
With that setup, you can include the Lacework plugin in your pipeline definition with the following format:
1 2 3 4 5 6steps: - label: "🕵️ Analysis" plugins: - lacework#v1.0.0: account-name: "YOUR_ACCOUNT_NAME" scan-type: "YOUR_SCAN_TYPE"
Where YOUR_SCAN_TYPE can be:
scaiacvulnerabilitysast
To perform an SCA scan, use the pipeline template or add the following to your pipeline definition:
1 2 3 4 5 6steps: - label: "🕵️ Lacework SCA scan" plugins: - lacework#v1.0.0: account-name: "YOUR_ACCOUNT_NAME" scan-type: "sca"
To perform an IaC scan with Terraform:
1 2 3 4 5 6 7steps: - label: "🕵️ Lacework IaC scan" plugins: - lacework#v1.0.0: account-name: "YOUR_ACCOUNT_NAME" scan-type: "iac" iac-scan-type: "terraform-scan"
To build a Docker image and perform a vulnerability scan:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15steps: - label: "🛠️ Build Docker image" command: ls plugins: - equinixmetal-buildkite/docker-build#v1.0.0: tags: - 'YOUR_IMAGE_NAME:latest' - label: "🕵️ Lacework container scan" plugins: - lacework#v1.0.0: account-name: "YOUR_COMPANY_NAME" scan-type: "vulnerability" vulnerability-scan-repository: "YOUR_IMAGE_NAME" vulnerability-scan-tag: "latest"
To perform a SAST Scan:
1 2 3 4 5 6steps: - label: "🕵️ Lacework SAST scan" plugins: - lacework#v1.0.0: account-name: "YOUR_COMPANY" scan-type: "sast"
The results from each build are sent to Lacework, where you can explore the information and start monitoring for issues. Every time you push code or open a pull request, Lacework will automatically scan your changes for vulnerabilities, misconfigurations, and other security risks.
For all the configuration options, see the plugin repository.
Moving from vulnerabilities to victories
You've read a lot about the benefits of integrating security into your DevOps pipelines with Lacework and Buildkite. But you know what they say—the proof is in the pudding (or in this case, the scanning).
So, what kind of real-world results can you expect? Consider the following scenarios.
Scenario 1: The dilemma of the dodgy dependency
You're working on a tight deadline, frantically coding away on your latest feature. You decide to use a new open-source library to speed things up. But unknown to you, that library has a critical vulnerability that could expose your application to attackers.
Luckily, you've integrated Lacework's SCA scanner into your Buildkite pipeline. As soon as you push your code, Lacework flags the vulnerable library and recommends a fix. Crisis averted!
Scenario 2: The mystery of the misconfigured infrastructure
You're spinning up a new AWS environment using Terraform. In your haste, you accidentally misconfigure an S3 bucket, leaving it open to public read access. Often, this might go unnoticed until an attacker stumbles upon your data.
But with Lacework's IaC scanner in your Buildkite pipeline, the misconfiguration is caught immediately. You can fix the issue before deploying, saving yourself from a potential data breach and a very awkward conversation with your CISO.
Scenario 3: The riddle of the risky container
Your team has been working hard on a new microservice, packaged up nicely in a Docker container. But you don't realize that your base image has some outdated OS packages with known vulnerabilities.
Lacework's container scanner detects vulnerable packages and provides a detailed report of the risks. Before pushing to production, you can update your base image and rebuild your container.
These are just a few examples, but you get the idea. By catching and fixing security issues early and often, you're not just saving yourself from potential disasters—you're also saving time, money, and a whole lot of headaches.
Plus, you're building a culture of security awareness within your team. When developers see the results of these scans in their Buildkite pipelines, they start to think more proactively about security in their day-to-day work.
Conclusion
Whether you're adopting DevSecOps for the first time or looking to optimize an existing practice, Buildkite provides the foundation for secure, high-velocity software delivery. Our open and flexible platform allows you to adapt and scale with your evolving security and compliance needs.
The Lacework plugin makes it easier to "shift security left" by embedding security into the software development lifecycle. That will help you avoid costly breaches, compliance violations, and reputational damage.
But remember, technology is only part of the equation. To truly succeed with DevSecOps, it takes a cultural shift. It means breaking down walls between teams, fostering collaboration, and making security a first-class citizen in your development process.
Get started today by signing up for a free trial with Lacework and adding the plugin to your CI/CD pipelines.
Buildkite Pipelines is a CI/CD tool designed for developer happiness. Easily follow and decipher logs, get observability into key build metrics, and tune for enterprise-grade speed, scale, and security. Every new signup gets a free trial to test out the key features. See Buildkite Pipelines to learn more.